Personal Authentication Settings - Level 2 and Level 3
Personal authentication settings allow a site to set up the additional authentication requirements over the Level 1 requirements defined. Different authentication requirements can be defined for a personal account. Also, the definition of a verified caller and authenticated caller is defined. For a list of available authentication options for level 2 and level 3 of Personal Authentication Options, please see section Authentication Options by Level.
Level 2 Personal Authentication Methods
Level 2 personal authentication method allows a site to choose one or more level 2 authentication options for personal accounts. There is no limit to the options that can be configured.
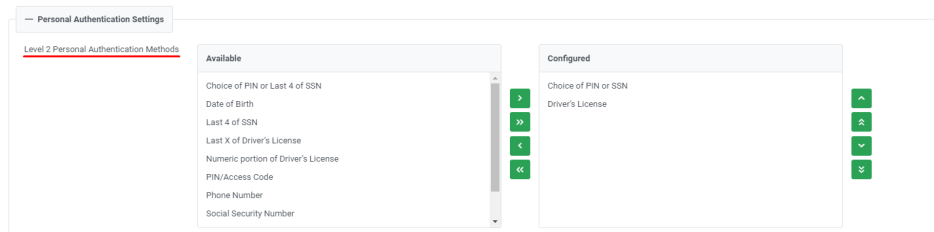
Adding Level 2 Personal Authentication methods
A list of authentication options is provided to choose and add to the profile. The list of options available depends on the core processing system used for the site. For a list of available options for core, please see Authentication Options by Core.
-
To add an authentication method, choose the authentication method using the pull-down list and click Add arrow.
-
To remove a chosen authentication method, choose the authentication method to be removed and, click Remove arrow.
-
To control the order of the authentication questions to be presented to the caller, move options up or down using the up or down arrows provided beside the Available authentication methods. The screen-listed order will be the method presented to the caller.
Level 3 Personal Authentication Methods
Level 3 personal authentication method allows a site to choose one or more level 3 authentication options for personal accounts. There is no limit to the number of options that can be used for authentication.
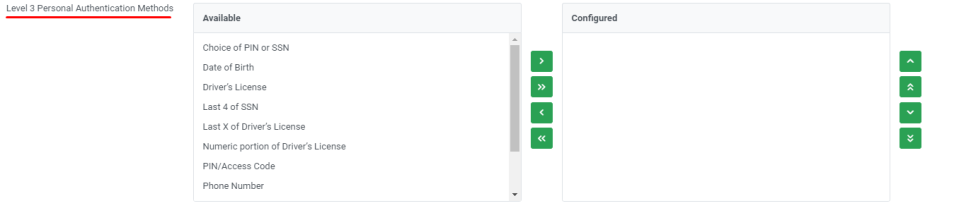
Adding Level 3 Personal Authentication Options
A list of authentication options is provided to choose and add to the profile. The list of options available depends on the core processing system used for the site. For a list of available options for your core, please see Authentication Options by Core.
To add an authentication method, choose the authentication method using the pull-down list and click Add arrow.
To remove a chosen authentication method, choose the authentication method to be removed and, click Remove arrow.
To control the order of the authentication questions to be presented to the caller, move options up or down using the up or down arrows provided beside the Available authentication methods. The screen-listed order will be the method presented to the caller.
Personal Caller Verified Requirements
The personal caller verified requirements allows the site to determine the authentication methods that must be correct to determine the caller is verified but not authenticated. The list of verified requirements available for selection will be a combination of the authentication methods chosen for level 2 and level 3.
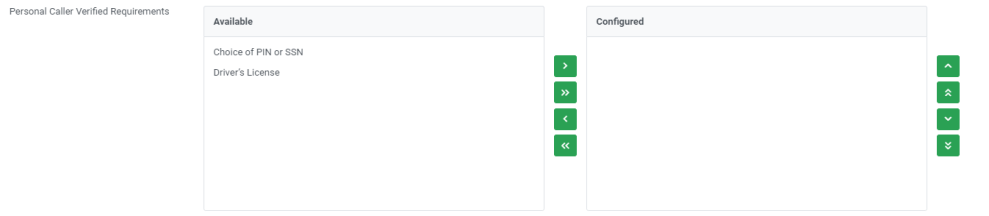
To add an authentication method to the verified list, choose the authentication method using the pull-down list and click Add arrow.
To remove a chosen authentication method, choose the authentication method to be removed and, click Remove arrow.
Personal Caller Authenticated Requirements
The personal caller authenticated requirements allows the site to determine the authentication methods that must be correct to determine the caller is authenticated. The list of authentication requirements available for selection will be a combination of the authentication options chosen for level 2 and level 3.
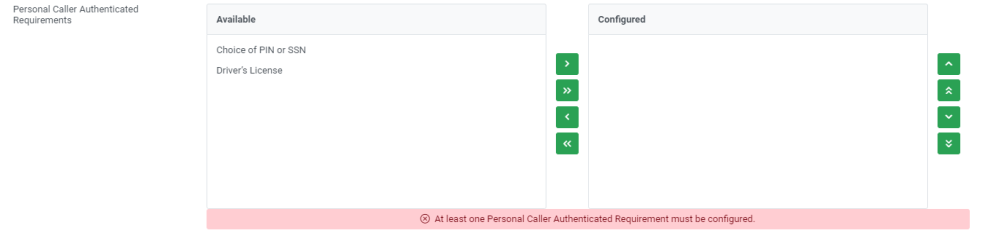
To add an authentication method to the authenticated list, choose the authentication method using the pull-down list and click Add arrow.
To remove a chosen authentication method, choose the authentication method to be removed and, click Remove arrow.
At least, one Personal Caller authentication requirement must be configured.
Comparison between Verified Requirements and Authenticated Requirements
The authentication system allows a site to define the difference between an authenticated caller and a verified caller.
A Verified Caller is a caller that has provided enough correct information to determine who the caller is but has not provided enough information to be considered authenticated.
An authenticated caller provided all the information required to be considered authenticated. On several products, the configuration will allow the site to indicate if the caller must be authenticated or verified to continue.
An important reason that a site wants to define the difference between authenticated and verified is for Screen Pop. If the caller is verified but not authenticated, the information can still be passed to the agent even if a positive authentication has not been made.
Level 1 authentication options are considered required for verification and authentication.